In today’s digital era, secure network access is no longer optional—it’s a necessity for businesses. Companies operate in hybrid work environments, rely on SaaS applications, and transmit sensitive data over public networks. Without the right security measures, cyber threats, credential theft, and data breaches become serious risks.
An internal network alone is not enough. Many organizations face accessibility challenges, whether due to employees working remotely, multiple branch offices, or geographical restrictions. A business VPN is a fundamental solution that ensures secure, flexible, and efficient access to corporate IT infrastructure while maintaining performance and compliance.
But what exactly is a VPN? Why is it a key element in modern corporate security? And how can businesses implement a VPN strategy effectively? Read on to find out how VPNs can secure business operations and how to choose the best solution for your company.
What is a VPN?
A Virtual Private Network (VPN) is a security technology that encrypts the connection between a user’s device and a corporate network or the internet. VPNs ensure that data remains protected and inaccessible to hackers, ISPs, or any other unauthorized entities attempting to intercept sensitive business information.
For companies, VPNs act as a secure bridge that allows employees, partners, and remote teams to access internal systems without the risk of data leaks or unauthorized access. Additionally, VPNs bypass geo-restrictions, ensuring uninterrupted, private, and secure connectivity.
How Does a VPN Work?
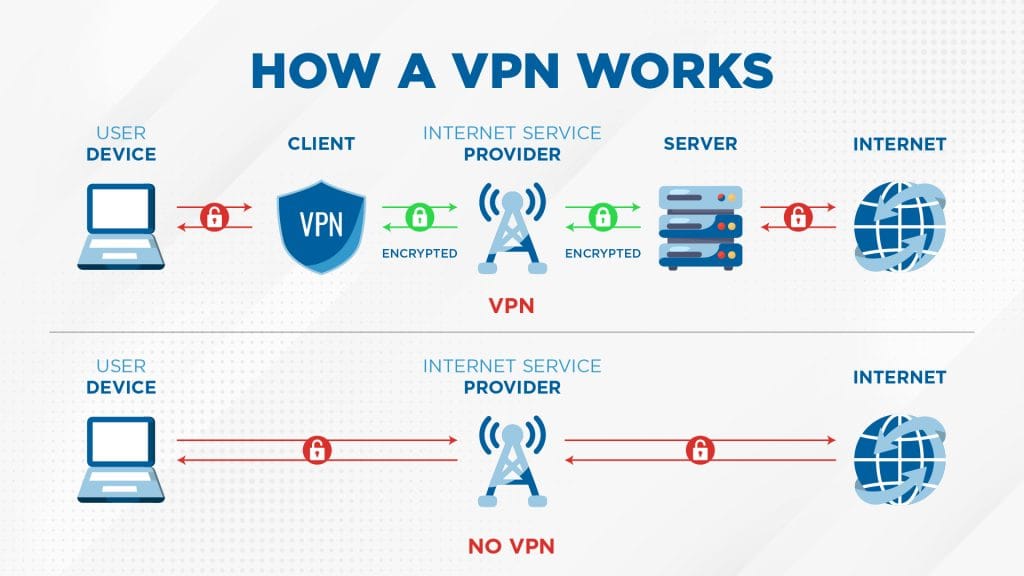
A VPN creates an encrypted communication tunnel between the user’s device and a VPN server before granting access to the corporate network or the internet.
Data Encryption
A VPN encrypts all traffic using AES-256-bit or ChaCha20 encryption, preventing third parties from intercepting or stealing sensitive data.
IP Masking
A VPN replaces the user’s actual IP address with the VPN server’s IP, enhancing privacy and preventing tracking or geographical restrictions.
Tunneling & Secure Protocols
VPNs use security protocols like L2TP/IPsec, OpenVPN, and WireGuard to create encrypted tunnels, safeguarding all data transmissions between devices and servers.
Multi-Factor Authentication (MFA)
Advanced business VPNs implement MFA as an additional security layer, ensuring that only verified users can access company networks.
Enterprise Security Integration
VPNs can be integrated with Identity Access Management (IAM) and Security Information and Event Management (SIEM) systems for enhanced visibility and security policy enforcement.
Why Do Businesses Need a VPN?
Network security is not an option—it is an essential part of IT infrastructure. A business VPN does more than protect data, it also improves efficiency, compliance, and connectivity across teams.
Secure Data Transmission
Without VPN encryption, business data is vulnerable to cyberattacks, particularly on unsecured Wi-Fi networks. A VPN prevents unauthorized access by securing data at every transfer point.
Safe Remote Access
VPNs allow employees to securely connect to corporate applications from anywhere, ensuring a safe remote and hybrid work experience.
Unified Connection for Branch Offices
Using Site-to-Site VPN, organizations can securely interconnect multiple branch offices under a single network without requiring expensive infrastructure.
Compliance with Security Regulations
VPNs help businesses stay compliant with international security standards, including ISO 27001, GDPR, NIST, and HIPAA, ensuring data privacy and regulatory adherence.
Who Needs a Business VPN?
VPNs are no longer exclusive to large enterprises. Any business that operates online should integrate a VPN into its cybersecurity framework.
Companies with Remote & Hybrid Teams
VPNs provide a secure gateway for employees accessing internal systems from external locations, eliminating exposure to public network risks.
Startups & Growing Businesses
Startups can implement enterprise-level security without the burden of high IT costs, allowing them to scale securely and efficiently.
Highly Regulated Industries
Sectors such as finance, healthcare, and government require strict compliance with security laws, making VPNs a necessity.
Enterprises with Global or Multi-Branch Operations
VPNs connect distributed teams securely, ensuring safe data transfers without geographical barriers or security threats.
Types of Business VPNs
Every company has unique network architectures and security needs. Choosing the right VPN requires considering factors such as business scale, operational models, and required security levels. Below are the most commonly used types of business VPNs.
Remote Access VPN
Designed for employees, business partners, or contractors who need secure access to the company’s internal network from an external location. This VPN requires a VPN client installed on the user’s device to establish an encrypted connection to the company’s servers.
Site-to-Site VPN
Enables multiple branch offices to share the same private network via an encrypted connection. This VPN is deployed on routers or firewalls in each location, linking one office’s local network to another’s without requiring VPN client installation on individual devices.
Cloud VPN
A cloud-based VPN solution that allows secure access to cloud applications and IT infrastructure without relying on an internal corporate network. This type is widely adopted by businesses implementing a cloud-first strategy or operating in multi-cloud environments.
Mobile VPN
Designed for users who frequently switch networks, such as field employees or traveling executives. Mobile VPN ensures continuous secure access, even when users move between Wi-Fi and cellular networks.
Challenges in Managing a Business VPN

While VPNs provide high-level security, improper implementation can lead to significant challenges for businesses. Here are some common difficulties encountered in managing business VPNs.
Complex User Management
As more users access the network through a VPN, managing authentication and access permissions becomes increasingly complex. Without proper control, businesses risk misconfigurations that can create security loopholes.
Credential Theft Risk
If VPN credentials are compromised or leaked, attackers can gain full access to the company’s network. This is a major challenge for organizations that have not yet implemented multi-factor authentication (MFA).
Limited Scalability
Traditional VPNs often experience bottlenecks when the number of users grows rapidly, especially in expanding businesses. Without a scalable architecture, performance can suffer, leading to slow connections and reduced efficiency.
Managing a VPN at a business scale isn’t just about providing secure connectivity—it’s about ensuring flexibility, efficiency, and ease of management. With challenges such as complex user management, credential theft risks, and scalability limitations, businesses require a more modern and adaptive VPN solution.
This is where Ivanti Connect Secure (ICS) comes in—a cutting-edge business VPN solution designed to offer maximum security, simplified management, and seamless accessibility for companies of all sizes.
Ivanti Connect Secure: A Smarter Business VPN Solution
Ivanti Connect Secure (ICS) is a comprehensive business VPN solution that integrates strict access control, high-level encryption, and a seamless user experience. ICS ensures that employees, business partners, and remote teams can securely connect to the company’s network without risking data leaks or cyber threats.
Key Features of Ivanti Connect Secure
ICS incorporates advanced security technologies to ensure safe, efficient, and reliable connectivity for businesses.
Multi-Factor Authentication (MFA)
Enhances security by implementing multi-layer authentication, including biometric verification, hardware tokens, and OTP codes, reducing the risk of credential theft.
Zero-Touch Provisioning
Fully automated deployment process, enabling businesses to activate VPN access on user devices without the need for complex manual configuration.
Adaptive Security Policies
Utilizes AI and machine learning to analyze user access patterns, detect anomalies, and automatically apply stricter access policies when suspicious activity is detected.
SSO & IAM Integration
Simplifies access management with Single Sign-On (SSO) and integration with Identity & Access Management (IAM) systems, ensuring that only authorized users can access company resources.
VPN Over SSL & IPsec Support
Offers various VPN connection methods, allowing businesses to choose between SSL and IPsec protocols, ensuring secure and flexible remote access.
Benefits of Ivanti Connect Secure
With robust security features, Ivanti Connect Secure helps businesses enhance productivity without compromising security.
Secure & Stable Network Access
ICS provides encrypted connections that protect against cyber threats, even when accessing networks from public Wi-Fi.
More Efficient User Management
A centralized dashboard allows IT administrators to manage user access, configure permissions, and monitor network activity in real-time.
Unlimited Scalability
Supports businesses of all sizes, from startups to large enterprises, with on-premise and cloud-based deployment options.
Compliance with Security Regulations
ICS helps businesses comply with global security standards such as ISO 27001, GDPR, and NIST, ensuring maximum data protection.
Explore More: Ivanti Solution on Virtus Technology Indonesia
Get the Best Business VPN Solution from Virtus Technology Indonesia
Virtus Technology Indonesia (VTI), as part of CTI Group, is ready to deliver the Ivanti Connect Secure (ICS) solution with professional and reliable services.
Supported by experienced and certified IT teams, Virtus will assist you throughout the entire implementation process—from consultation, deployment, and management to aftersales support. We ensure optimal system performance to maintain smooth business operations.
Interested? Click here to get a FREE consultation, free trial, and a live demo of Ivanti Connect Secure with Virtus today!
Author: Danurdhara Suluh Prasasta
CTI Group Content Writer



























