In a world where cyber threats are advancing rapidly, securing your organization’s digital assets isn’t just a necessity—it’s a matter of survival. From small startups to global enterprises, every business is at risk of cyber threat. The NIST Cybersecurity Framework helps organizations manage cybersecurity risks and fortify defense.
But what exactly is this framework, and how can it bolster your defenses against the relentless tide of cyber threats? Buckle up as we dive deep into the NIST Cybersecurity Framework, unpack its core components, and explore how it can revolutionize your approach to cybersecurity.
What is the NIST Cybersecurity Framework?
At its core, the NIST Cybersecurity Framework is a set of voluntary guidelines designed to help organizations manage and reduce cybersecurity risk. Developed by the National Institute of Standards and Technology (NIST), this framework provides a common language and systematic methodology for managing cybersecurity risks, allowing organizations to better understand, communicate, and manage their cybersecurity efforts.
It’s not just another IT checklist—it’s a dynamic, flexible tool that adapts to your organization’s unique needs, risk profile, and resources. Whether you’re a tech giant or a small business venturing into the digital realm, the NIST Framework offers a scalable approach to safeguarding your digital assets.
A Brief History of the NIST Cybersecurity Framework
The genesis of the NIST Cybersecurity Framework is rooted in a growing recognition of the need for robust cybersecurity standards. In 2013, a series of high-profile cyber-attacks on critical infrastructure prompted President Obama to issue Executive Order 13636, calling for the development of a framework to improve cybersecurity across industries.
NIST answered the call by collaborating with industry experts, government agencies, and academia to create the initial version of the framework, released in 2014. This collaborative approach ensured that the framework was grounded in real-world challenges and practical solutions.
Since its inception, the framework has evolved to address emerging threats and technologies. The most recent version continues to serve as a cornerstone for organizations striving to enhance their cybersecurity posture in an increasingly digital world.
Why is the NIST Cybersecurity Framework Important?
Businesses are embracing digital technologies to drive innovation and growth. However, this digital transformation comes with increased exposure to cyber risks. The NIST Cybersecurity Framework is crucial because it helps organizations:
- Understand and Manage Risks: It provides a structured approach to identifying and mitigating cybersecurity risks tailored to your organization’s specific context.
- Enhance Resilience: By addressing not just prevention but also detection and response, the framework helps organizations build resilience against cyber incidents.
- Facilitate Communication: It offers a common language for discussing cybersecurity issues internally and with external partners, fostering better collaboration.
- Ensure Compliance: Aligning with the framework can help organizations meet regulatory requirements and industry standards.
NIST Cybersecurity Framework Structure
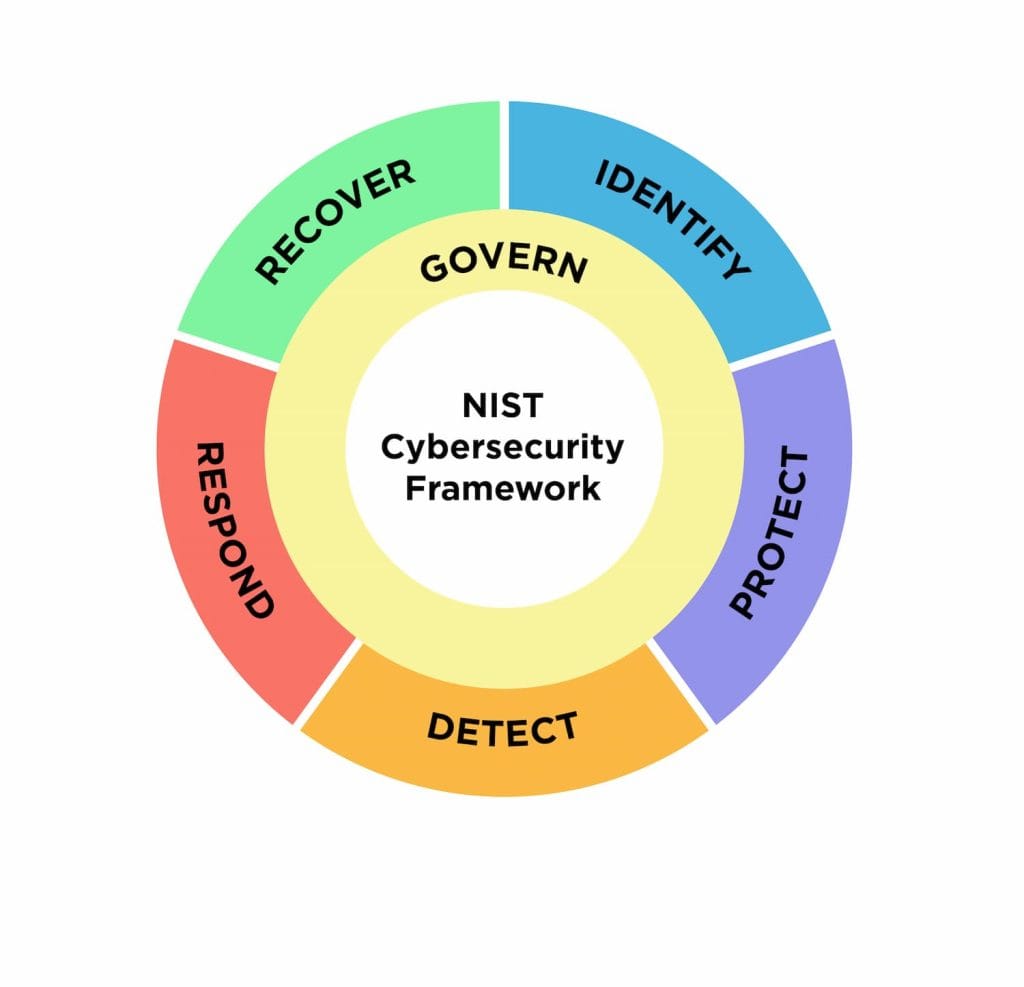
Source: NIST Cybersecurity Framework
The framework is organized into five core functions that represent the high-level cybersecurity activities in an organization. Think of these functions as pillars supporting your cybersecurity strategy:
1. Identify
The Identify function is all about gaining a deep understanding of your organizational context, resources, and risks. This involves:
- Asset Management: Cataloging your physical and digital assets.
- Business Environment: Recognizing the organization’s role in the supply chain and critical functions.
- Governance: Establishing policies and procedures for cybersecurity.
- Risk Assessment: Identifying potential threats and vulnerabilities.
Common Challenge: Many organizations struggle with lack of visibility into their assets, leading to unmanaged risks.
Implementation Example: Conduct regular audits to maintain an up-to-date inventory of all hardware, software, and data assets, assessing their criticality and vulnerability.
2. Protect
The Protect function outlines appropriate safeguards to ensure the delivery of critical services. Key activities include:
- Access Control: Managing permissions and user access.
- Awareness and Training: Educating employees about cybersecurity best practices.
- Data Security: Implementing encryption and data loss prevention measures.
- Protective Technology: Deploying firewalls, antivirus software, and intrusion prevention systems.
Common Challenge: Human error is a significant factor in security breaches due to inadequate training.
Implementation Example: Implement multi-factor authentication (MFA) and conduct regular employee training sessions on recognizing phishing attempts.
3. Detect
The Detect function focuses on timely discovery of cybersecurity events. This involves:
- Anomalies and Events: Monitoring unusual activities.
- Continuous Monitoring: Keeping an eye on networks and systems in real-time.
- Detection Processes: Establishing alert thresholds and response protocols.
Common Challenge: Organizations often face an overwhelming volume of security alerts, making it hard to identify genuine threats.
Implementation Example: Use advanced analytics and machine learning to filter out false positives and highlight critical alerts for immediate action.
4. Respond
The Respond function involves developing and implementing strategies to contain and mitigate the impact of cybersecurity incidents. Activities include:
- Response Planning: Having an incident response plan in place.
- Communications: Coordinating with stakeholders and authorities.
- Analysis: Understanding the incident to prevent future occurrences.
- Mitigation: Implementing measures to stop the spread and impact of the incident.
Common Challenge: Delayed response due to lack of a clear plan can exacerbate the damage from an incident.
Implementation Example: Establish an incident response team and conduct regular drills to ensure readiness.
5. Recover
The Recover function supports timely recovery to normal operations and includes:
- Recovery Planning: Developing strategies to restore capabilities.
- Improvements: Learning from incidents to improve resilience.
- Communications: Keeping stakeholders informed during recovery actions.
Common Challenge: Recovery efforts can be hampered by insufficient backups or untested recovery procedures.
Implementation Example: Regularly back up critical data to secure, offsite locations and test recovery processes to ensure they work when needed.
Benefits of Implementing the NIST Cybersecurity Framework
Embracing the NIST Cybersecurity Framework offers numerous benefits:
- Enhanced Security: A holistic approach that covers all aspects of cybersecurity.
- Risk Management: Prioritize risks and allocate resources efficiently.
- Regulatory Compliance: Simplifies meeting legal and industry-specific security requirements.
- Improved Communication: Facilitates better communication across your organization and with external partners.
- Resilience: Increases your ability to withstand and recover from cyber incidents, reducing downtime and potential losses.
Integrating Cutting-Edge Solutions with the NIST Framework
While the NIST Cybersecurity Framework provides a solid foundation, integrating advanced security solutions can take your cybersecurity posture to the next level.
Virtus Technology Indonesia offers a range of cutting-edge solutions designed to align with the framework’s core functions, helping you fortify your defenses and achieve a more robust security posture.
Dell Cyber Recovery
In the event of a catastrophic cyberattack, having a secure, isolated recovery environment can be the difference between a minor setback and a major disaster.
Dell Cyber Recovery, offered by Virtus, provides an air-gapped vault for your critical data, ensuring that even if your primary systems are compromised, you have a clean copy to fall back on. With immutable backups and automated recovery processes, you can minimize downtime and get back to business quickly.
Forcepoint NGFW
Your network perimeter is your first line of defense against cyber threats. Forcepoint Next-Generation Firewall (NGFW), available through Virtus, acts as a vigilant gatekeeper, combining advanced firewall capabilities with intrusion prevention, malware detection, and deep content inspection.
By monitoring and controlling traffic across your network, Forcepoint NGFW can detect and block potential threats before they can wreak havoc on your systems.
SolarWinds
You can’t protect what you can’t see. SolarWinds, part of Virtus’ solution portfolio, provides a comprehensive suite of network monitoring and management tools that give you complete visibility into your IT infrastructure.
With features like real-time performance monitoring, network traffic analysis, and security event logging, SolarWinds helps you identify potential issues and respond quickly to minimize the impact of any incidents.
Virtus: Your Ideal IT Partner for Implementing the NIST Cybersecurity Framework
Navigating the complexities of cybersecurity can be daunting, but you don’t have to go it alone. Virtus Technology Indonesia is here to help you turn the NIST Cybersecurity Framework from concept into reality.
Implementing the NIST Cybersecurity Framework can elevate your organization’s security to new heights, ensuring resilience in the face of evolving cyber threats. By partnering with Virtus and utilizing industry-leading solutions from Dell, Forcepoint, and SolarWinds, you’re not just adopting a framework—you’re investing in the future of your business.
Don’t wait until a cyber incident forces your hand. Take proactive steps now to safeguard your assets, maintain customer trust, and secure your competitive edge.
Contact Virtus Technology Indonesia today to learn how we can tailor the NIST Cybersecurity Framework to fit your organization’s unique needs. Let’s work together to build a robust cybersecurity strategy that empowers your business to thrive in the digital age.
Author: Jeko Reza
Content Writer – CTI Group



























